About 32,385 results found.
(Query 0.02600 seconds)
- All
- Images
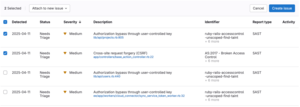
Attach vulnerabilities to a new issue
dacxzjk3kq5mmepbdd3ai2ifynlzxsnpl2cnkfhridqfywihrfftapid.onion

Hacking Techniques: How a Hacker Exploit Vulnerabilities
apqcqk4gowcm2lgltggrouxjwvmatzlwumyvir25ptzuzltyb5u5c2yd.onion

In this diagram, the computer uses a VPN, which encrypts its traffic and connects to iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion. The network router and Internet Service Provider might see that the computer is using a VPN, but the data
ssd.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Out with the old and in with the new – Goodbye Gmail!
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Secure Access to the Dark Web and Hidden Wiki
rgq674vzdxkj2rsk6rjxjjeuw2kzt3u56g56pafijr66vea5wios76ad.onion

An eye, watching traffic going in and out of a home network router.
ssd.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Giant face watching a concerned patient and doctors through a window
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
Free secure desktop email client for Linux, Windows and macOS.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

In this diagram, the request for iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion’s IP address is modified at the Internet Service Provider level. The ISP interferes with the DNS resolver, and the IP address is redirected to give an incorrec
ssd.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
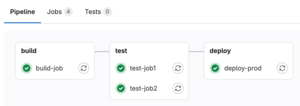
The pipeline graph shows each job, its status, and its dependencies across all stages.
dacxzjk3kq5mmepbdd3ai2ifynlzxsnpl2cnkfhridqfywihrfftapid.onion
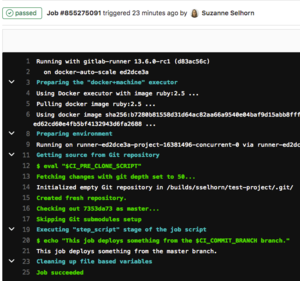
The job details page shows the current status, timing information, and the output of logs.
dacxzjk3kq5mmepbdd3ai2ifynlzxsnpl2cnkfhridqfywihrfftapid.onion

Risks of Hiring a Dark Web Hacker: What to Be Aware Of
apqcqk4gowcm2lgltggrouxjwvmatzlwumyvir25ptzuzltyb5u5c2yd.onion

Ethical Considerations of Hacking Messaging Apps: A Deep Dive
apqcqk4gowcm2lgltggrouxjwvmatzlwumyvir25ptzuzltyb5u5c2yd.onion

Hire a hacker to erase criminal records
torzcd47rw4qh36g4yqxvv2tmifgmu6jjalkyqz4e4lzzwtfdfc7qaqd.onion

List of organisations that we share common goals with
fsfeorg3hsfyuhmdylxrqdvgsmjeoxuuug5a4dv3c3grkxzsl33d3xyd.onion

A graphic showing a secure HTTPS request for "https://iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion/deeplinks" from a device. The site is revealed to your network administrators and your ISP, but they can't see the page you're v
ssd.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

1_c8e6ea40-c9d4-4932-8480-6ed2233a49b6_grande
cashcarkb36sln3vyw3sfz42c2kpzcp5twwr32rlr4lbym6rwyx553qd.onion
Phone with ears extending out of the sides of the device and the text "Is My Phone Listening to Me?"
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
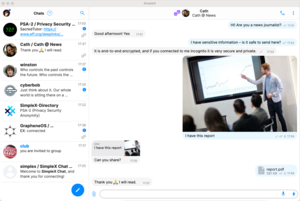
Up-and-coming Decentralized WhatsApp Alternative: SimpleX.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
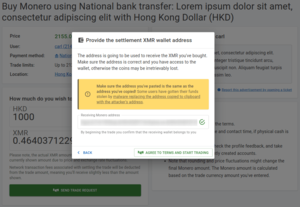
buy monero ad details, terms of trade and trade amount input
ejsx3rexkkaxrwe3dol2lml42fug7mxze3aoayshbj7vjhopng6uwlyd.onion
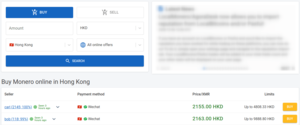
buy monero online: search options to select currency, country and payment method
ejsx3rexkkaxrwe3dol2lml42fug7mxze3aoayshbj7vjhopng6uwlyd.onion
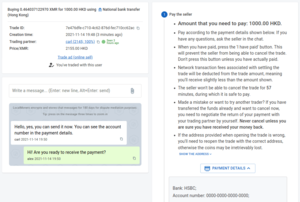
buying monero online trade window, showing chat, trade status and 'I have paid' button
ejsx3rexkkaxrwe3dol2lml42fug7mxze3aoayshbj7vjhopng6uwlyd.onion

Viola and Yara Palestinian Christians
a272fk5d36p7qbmdgcf5d4dwwmhncdkteqmnzbercp75hgycbmytb4ad.onion

3 types of trackers on green and orange backgrounds
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
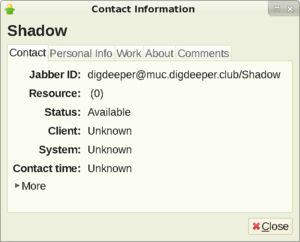
Screenshot showing falsified system and client in Psi+
us63bgjkxwpyrpvsqom6kw3jcy2yujbplkhtzt64yykt42ne2ms7p4yd.onion
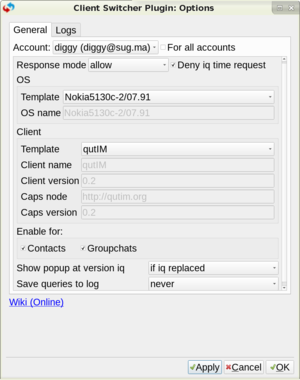
Screenshot showing Psi+ falsification of client and system information
us63bgjkxwpyrpvsqom6kw3jcy2yujbplkhtzt64yykt42ne2ms7p4yd.onion

Eckmar 10.34 Pro: Powered by Laravel 10.34 and PHP 8.2.8
onionxbxjz52g2yfhnulicwt7qvqimjgrkujtredpgc3ypjqboiiynyd.onion

Pablo Escobar Market Reputed and Reliable
zdacwobtzwp2xgedcv2besrckdq76um5xdyvaqcedatzqxbjewamheyd.onion

Facts about Bitcoin Mixing and Bitcoin Blending
coino2q64k4fg3lkjsnhjeydzwykw22a56u5nf2rdfzkjuy3jbwvypqd.onion

Cryptocurrency and the World of Bitcoin Mixer
coino2q64k4fg3lkjsnhjeydzwykw22a56u5nf2rdfzkjuy3jbwvypqd.onion

An array of laptops, each with a virus image, except three, which have an icon for EFF's main issues: free speech, privacy and innovation.
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion