About 11,574 results found.
(Query 0.00200 seconds)
- All
- Images

icon of a border agent examining digital devices
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Tarah Wheeler, EFF Board of Directors
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Tuta Calendar: verfügbar auf Android, iPhone, Linux, Windows, macOS und im Browser.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
OurCal: verschlüsselter Gruppenkalender.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Report a pattern - darkpatternstipline.org
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

US flag with spying eyes for stars
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

US flag with spying eyes for stars
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
When storing and sharing large files online, the data must be secured with post-quantum secure encryption.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Internet Censorship in Indonesia
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
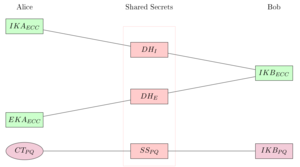
TutaCrypt key exchange: shared secret calculation
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Quantum-resistant encryption is what we need to develop now!
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Protect your data from quantum computer attacks with post-quantum encryption.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Microsoft got hacked by China, and a new report draws a devastating conclusion.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Unlike the telephone and post which have had their day and faded out of fashion, email has no expiry date! Sending emails will remain the constant form of online communication.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

After one too many data breaches, just how safe is Dropbox?
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Do the right thing, EU: Put. Down. My. Phone.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

US Senator Marsha Blackburn pushes dangerous KOSA legislation that would hurt free speech.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

UNREDACTED Magazine Issue 005 – IntelTechniques Blog
torzcd47rw4qh36g4yqxvv2tmifgmu6jjalkyqz4e4lzzwtfdfc7qaqd.onion

an eye covers a globe in multi-hued background
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

hands with circuit patterns on black background
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Old Big Tech email solutions: Know your risks and switch to more secure alternatives.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
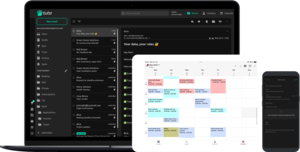
Screenshot von Tuta Mail und Tuta Calendar
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
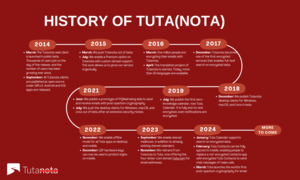
Geschichte von Tuta(nota): Erfolge von 2014 - 2024
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Tutanota encrypted email client in 2020
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion