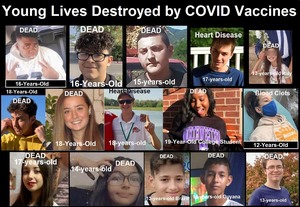
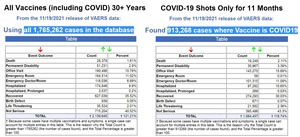
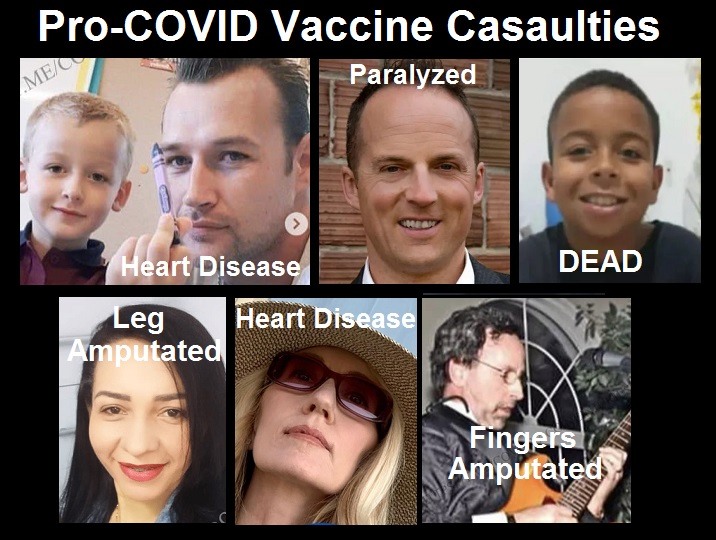
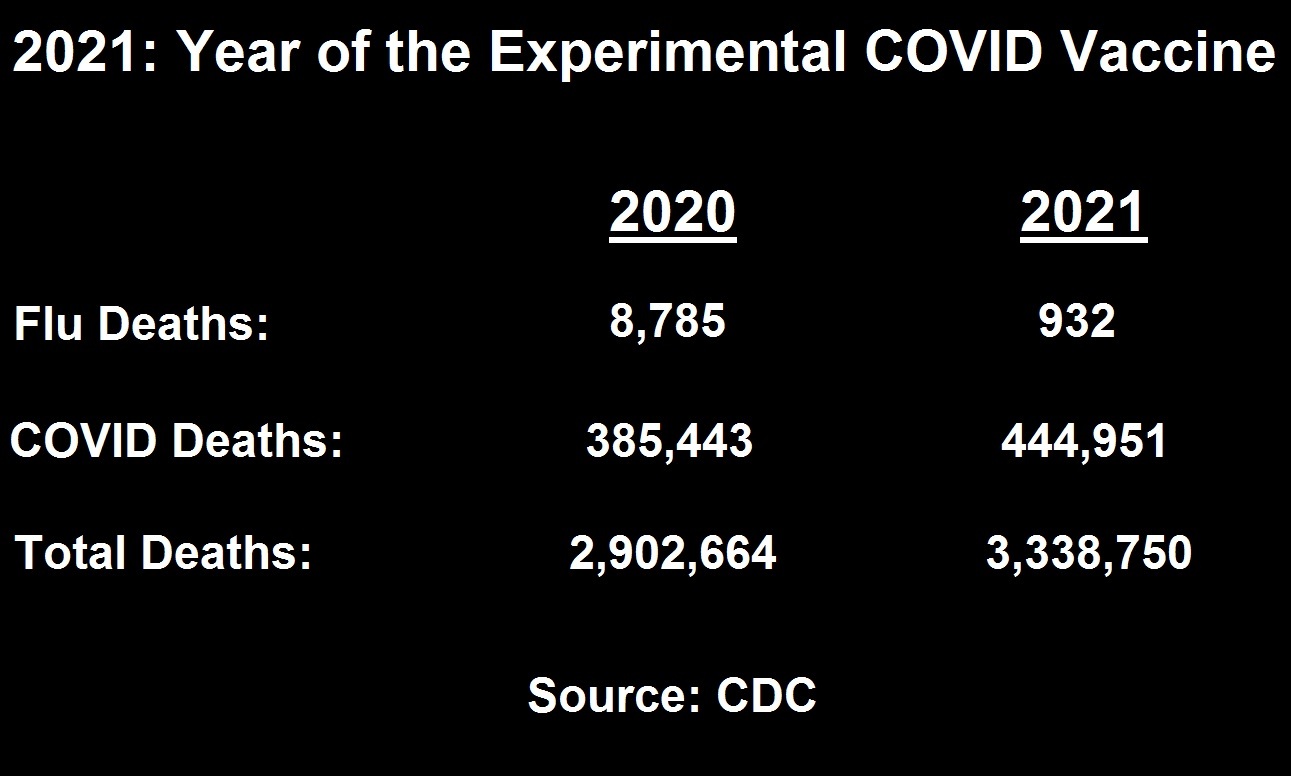
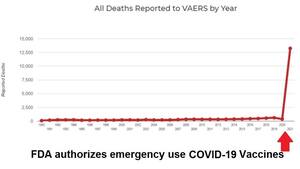
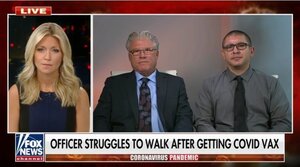
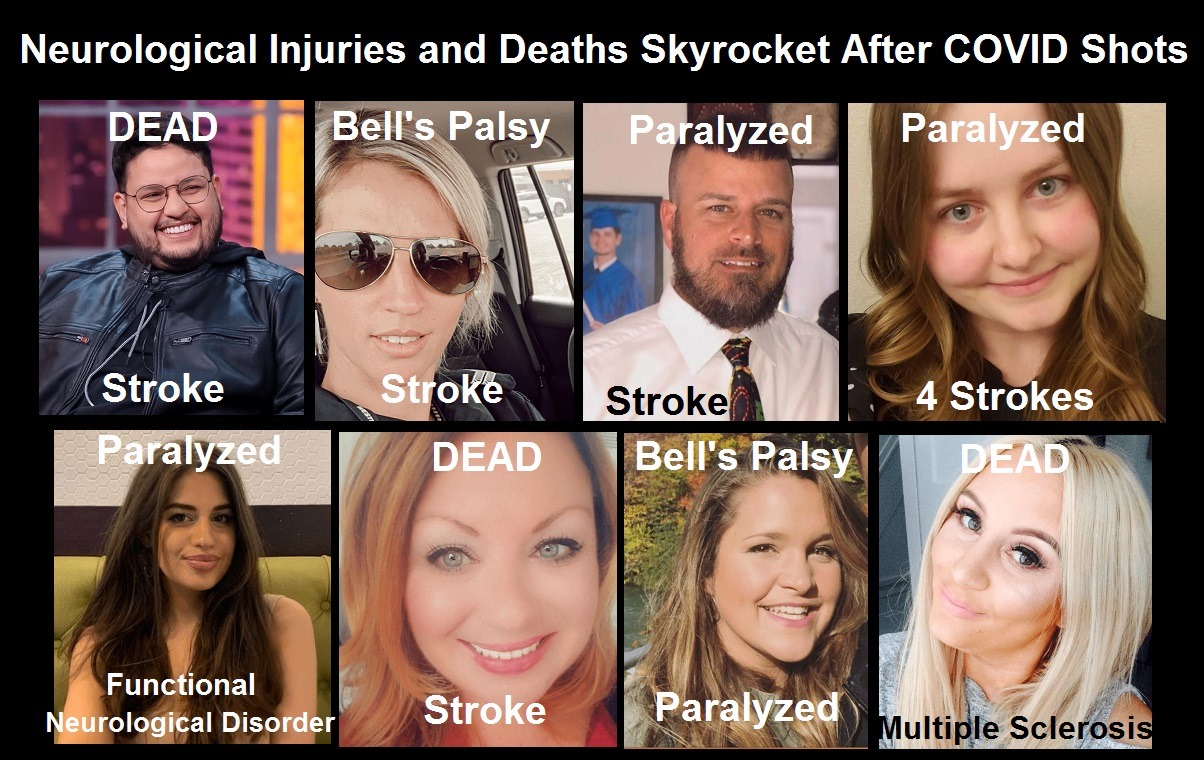
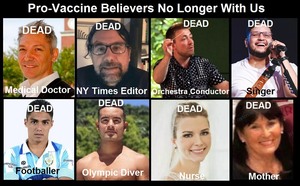
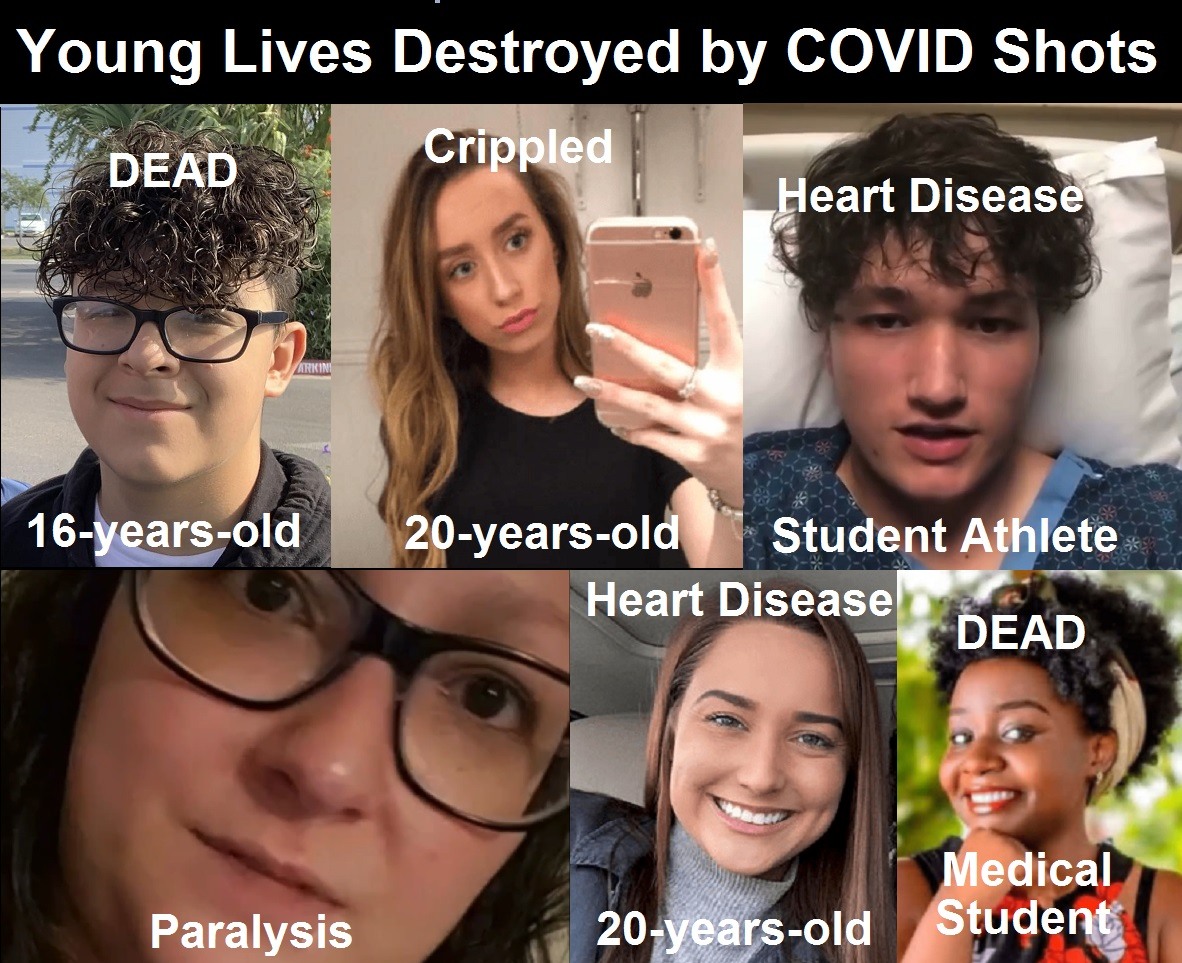
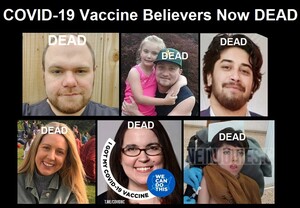
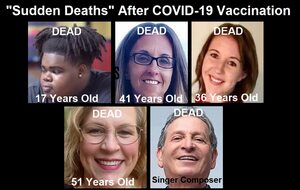
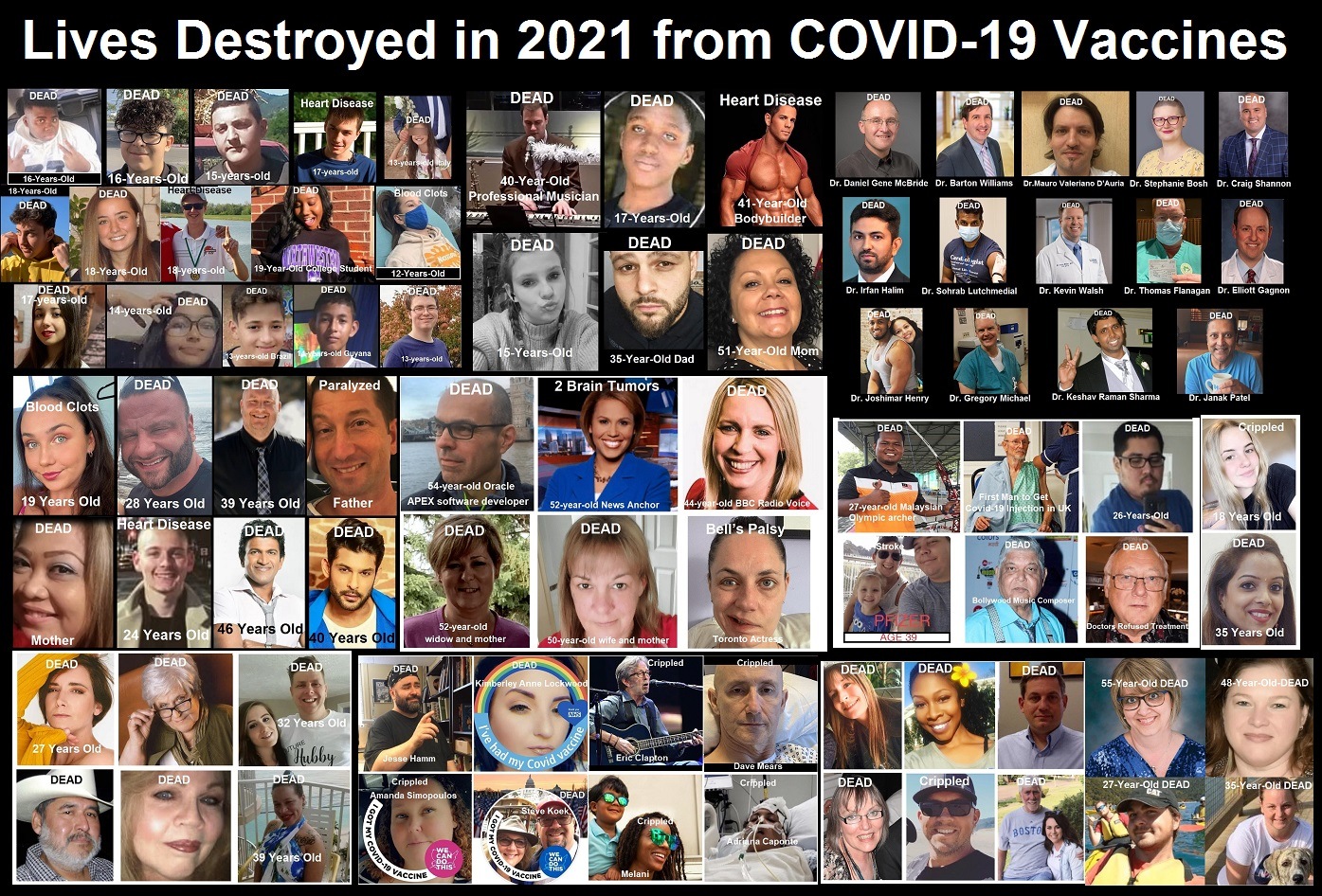
About 16,173 results found.
(Query 0.01800 seconds)
- All
- Images

Josh Sabey and Sarah Perkins with children
a272fk5d36p7qbmdgcf5d4dwwmhncdkteqmnzbercp75hgycbmytb4ad.onion

Happy Family. Mother Holding Small Child. Family Concept. Woman
a272fk5d36p7qbmdgcf5d4dwwmhncdkteqmnzbercp75hgycbmytb4ad.onion