About 5,691 results found.
(Query 0.01800 seconds)
- All
- Images

Bar Graph shows the comparison of energy usage of Bitcoin and various industries.
www.buskillvampfih2iucxhit3qp36i2zzql3u6pmkeafvlxs3tlmot5yad.onion
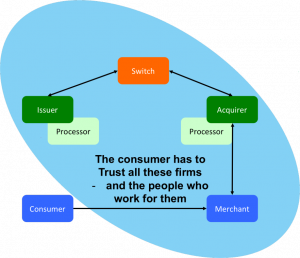
Diagram shows all the third parties that can steal your funds in a pull-based system: Merchant, Acquierer, Payment Processor, Switch, Issuer
www.buskillvampfih2iucxhit3qp36i2zzql3u6pmkeafvlxs3tlmot5yad.onion

Tweet from WikiLeaks that reads "WikiLeaks now accepts anonymous Bitcoin donations on 1HB5XMLmzFVj8ALj6mfBsbifRoD4miY36v"
www.buskillvampfih2iucxhit3qp36i2zzql3u6pmkeafvlxs3tlmot5yad.onion

Kennedy Malone Kirsch future political leaders
a272fk5d36p7qbmdgcf5d4dwwmhncdkteqmnzbercp75hgycbmytb4ad.onion

Hyperinflation Economy And Global Inflation Concept Or Overvalue
a272fk5d36p7qbmdgcf5d4dwwmhncdkteqmnzbercp75hgycbmytb4ad.onion
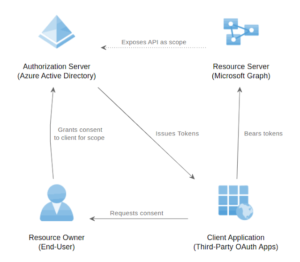
Cross-Platform Framework For Enumerating, Spraying, Exfiltrating, And Backdooring O365 AAD Accounts
torzcd47rw4qh36g4yqxvv2tmifgmu6jjalkyqz4e4lzzwtfdfc7qaqd.onion

4 icons representing saving News from big tech
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion