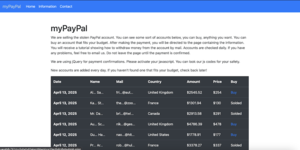
About 19,023 results found.
(Query 0.01100 seconds)
- All
- Images

Headshot of Lisa Femia standing outside of the EFF office
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

A public domain illustration od Don Quixote de la Mancha.
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

woman with pink hair and glasses smiling at the camera
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Methamphetamine hydrochloride synthesis via Leuckart amination
mumxbkms57zlmezjvdjj63cffd2fgzsvjv3sc5muzeptqyx5er7bxqqd.onion
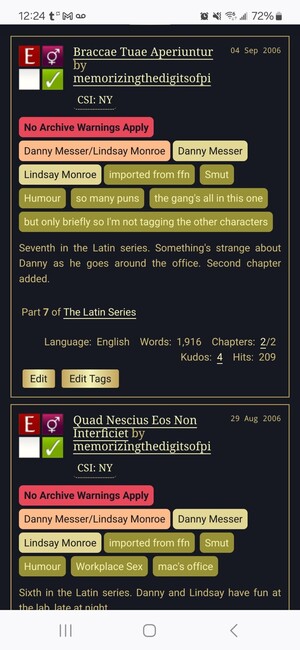
Examples of work blurbs. Each tag is contained inside a box. The boxes are coloured according to their tag type. Warnings are red, Relationships are peach, Characters are light gold, Additional tags are yellow-green
priviblur.bunny5exbgbp4sqe2h2rfq2brgrx3dhohdweonepzwfgumfyygb35wyd.onion
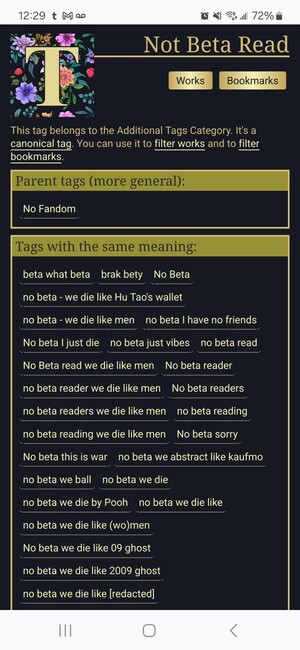
Not Beta Read tag page. The T icon has been replaced with a golden T on a floral background. Each section of the tag description is contained in a box with a yellow-green outer border.
priviblur.bunny5exbgbp4sqe2h2rfq2brgrx3dhohdweonepzwfgumfyygb35wyd.onion
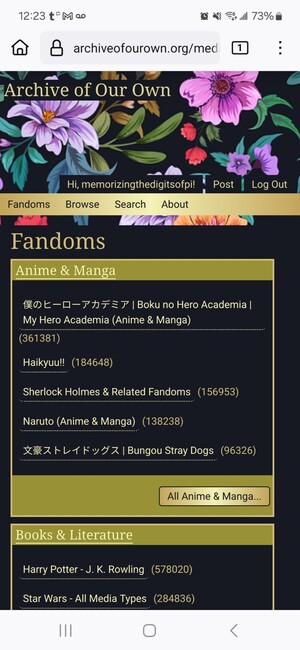
The All Fandoms page, showing each box with a yellow-green outer frame. Links are a lighter gold and regular text is a darker gold.
priviblur.bunny5exbgbp4sqe2h2rfq2brgrx3dhohdweonepzwfgumfyygb35wyd.onion
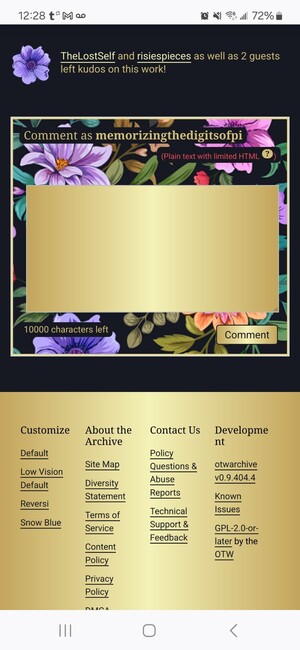
Kudos icon is replaced by one of the flowers from the pattern in the header. The comment box has the same floral border. The text entry box is gold, as is the comment button. The footer is gold with black text.
priviblur.bunny5exbgbp4sqe2h2rfq2brgrx3dhohdweonepzwfgumfyygb35wyd.onion