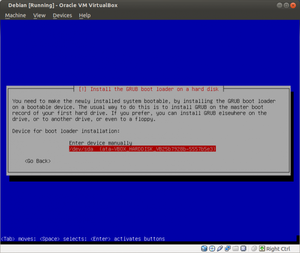
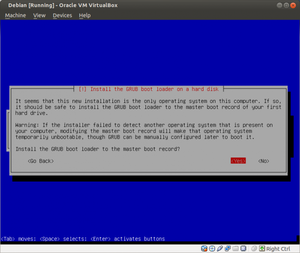
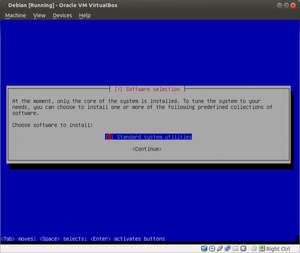
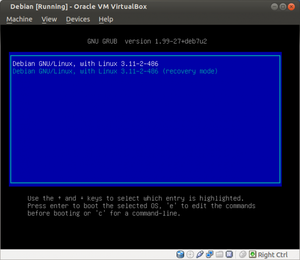
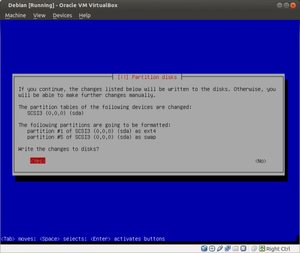
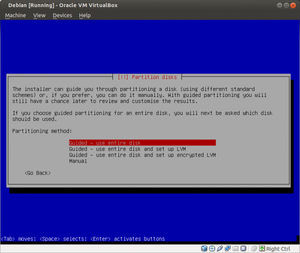
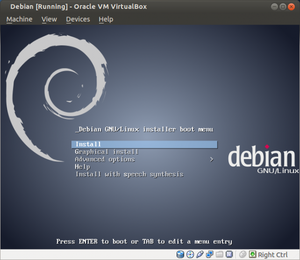
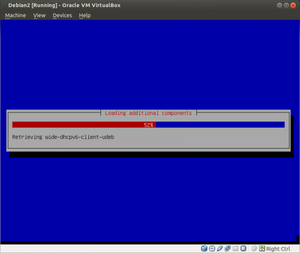
About 10,421 results found.
(Query 0.01600 seconds)
- All
- Images

illustration of a hammer and a wrench
annualreport.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
screenshot of Onion Tor Search Engines (V3) - http://deepwebyl3au3fnm4efynncy5fhiqknam3op6q3qgdwu3n5oavofifqd.onion/onion-tor-search-engines-v3
justdirs5iebdkegiwbp3k6vwgwyr5mce7pztld23hlluy22ox4r3iad.onion

BITCOIN MINING MACHINEbrand new Bitmain Antminer APW12 spare power supply
lionznqc2hg2wsp5vgruqait4cpknihwlje6hkjyi52lcl5ivyf7bcad.onion
screenshot of VORON CARD - rw6dbj2efldwrrak6xeuc7j33k74toa2mvhghkzzmkh7dxiu7ixcadad.onion
uzsafbditdon2fgpw7f4rqzjkduofe3zlvx5v5cbtvb57sa3jktejpqd.onion
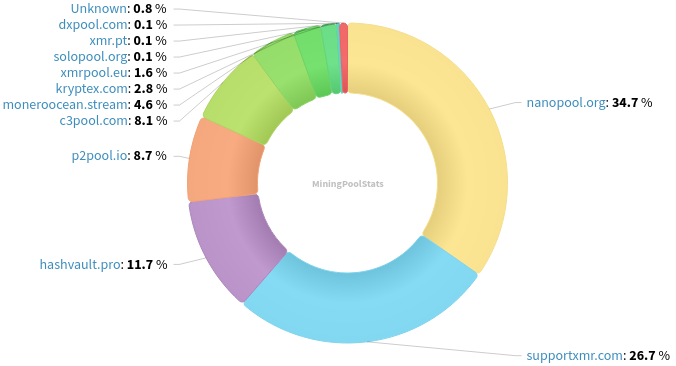
Hashrate Pool Distribution Pie Chart
gitea.recanman7nly4wwc5f2t2h55jnxsr7wo664o3lsydngwetvrguz4esid.onion

Buy MSI Radeon RX 5700 from the trusted seller Stop Game | TorBuy - The best escrow marketplace with verified sellers.
torbuyec4aetakqpuw4tnvkimrl77tj4qrhx74mgmu6lqmdxvp27jqyd.onion