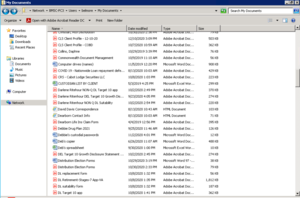
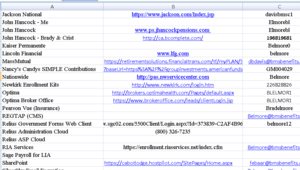
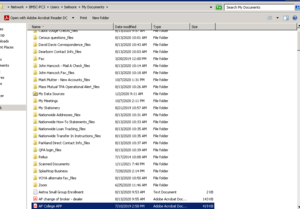
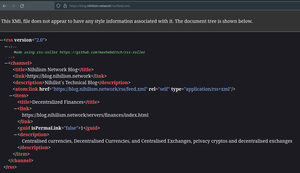
About 9,983 results found.
(Query 0.00200 seconds)
- All
- Images

EFF logo with a crowned DEF CON skull in the middle.
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

2024 EFF Award honorees and guest speakers
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Dogs playing at the EFF Benefit Poker Tournament table
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

A vivid global logistics scene with buy bitcoin symbols, showcasing Coinmama's role in international trade.
coinmamailtcrg7fw6uorut3d35bk35rtmntkrtb4fgeov6pefvfutqd.onion

The Complete Guide to Bitcoin: Price, Value, and Future Predictions
kddlbchlmhn3zwitoh6h7xbfancfbpuz2qfadwzh5eigj3hxzm32t5id.onion