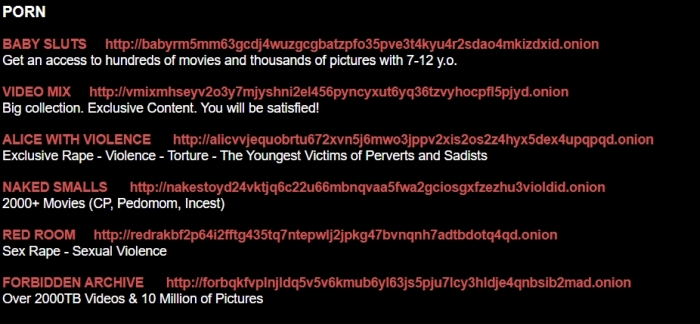
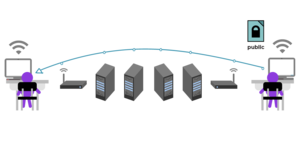
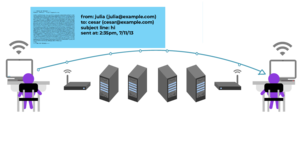
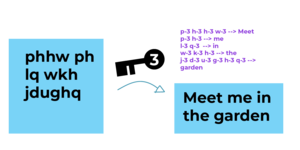
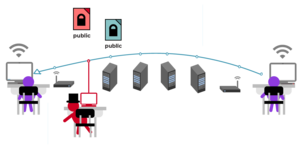
About 5,691 results found.
(Query 0.00500 seconds)
- All
- Images
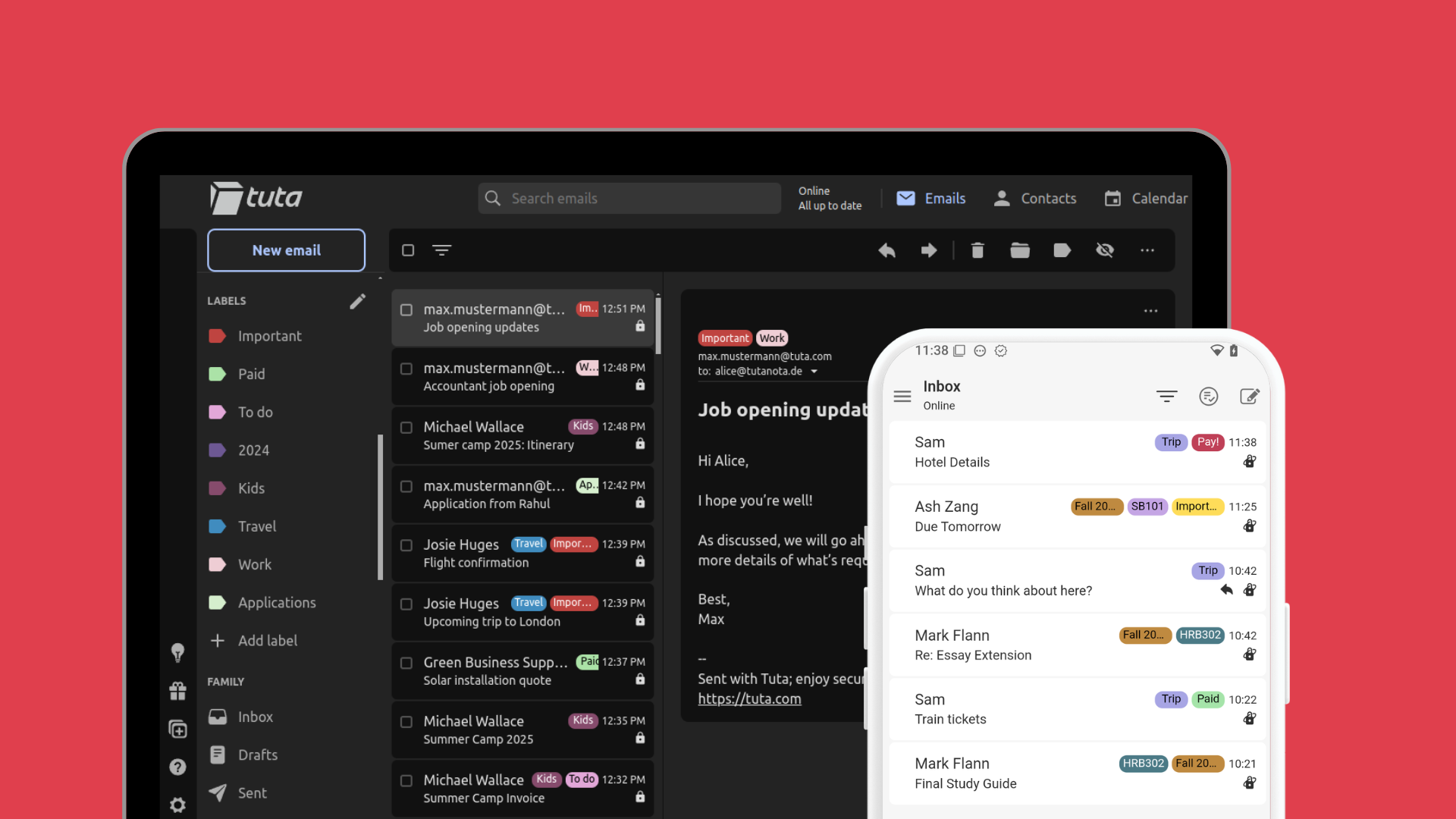
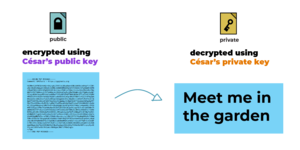
Labels in Tuta Mail let you organize your encrypted mailbox seamlessly.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

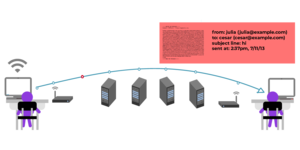
Transparency Report & Warrant Canary for the secure email service Tuta (formerly Tutanota)
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Das gesamte Tuta-Team setzt sich für den Schutz Ihrer Privatsphäre ein.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Tirdad kernel module for random ISN generation
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion

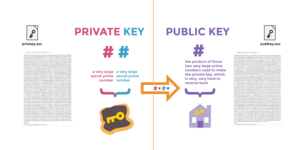
Complete respect for privacy and user freedom
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion

A Walnut Creek Police Department speed trailer with an automated license plate reader attached.
sls.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Automated License Plate Readers
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion