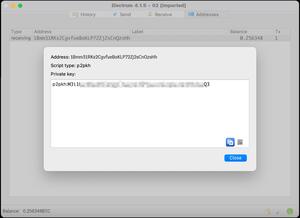
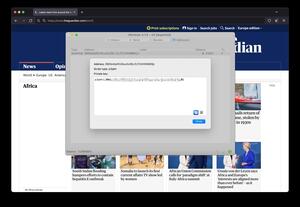
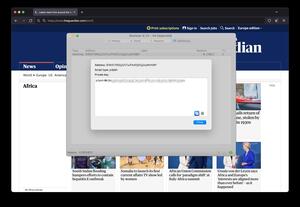
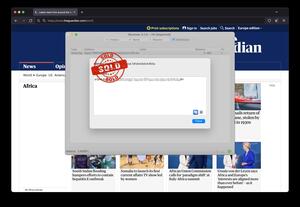
About 8,078 results found.
(Query 0.01100 seconds)
- All
- Images

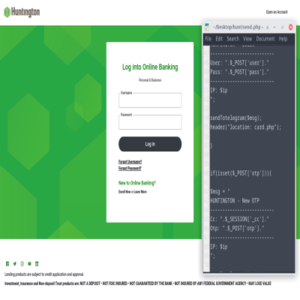
We are a group of 30+ individual freelance hackers ready to help you 24/7. We provide a wide range of hacking services. Below is a list of our most requested services. We are ready to fulfill your requirments, contact us
spyingztlrmrnxuv77sn4sjgp5lcqzpvm4los4fxkery2b73gab2tmqd.onion
Tuta Calendar updates: Advanced repeat rules, three-day view and calendar name in event preview.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion