About 11,454 results found.
(Query 0.00600 seconds)
- All
- Images
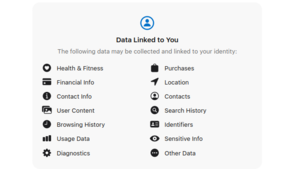
Threads data linked to you. Source: Apple App Store
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

bitcoin super pump 4.2.9 the ultimate bitcoin generatro
dreamr6y7e7ilemgws2ccuegvwdge3sfdm2ijh4s4hc2eggz3cvgl2ad.onion
screenshot of Forums boards chans Wiki Links v3 - http://vykenniek4sagugiayj3z32rpyrinoadduprjtdy4wharue6cz7zudid.onion/dir/boards-chans.html
justdirs5iebdkegiwbp3k6vwgwyr5mce7pztld23hlluy22ox4r3iad.onion

SIG Sauer P-220 9mm Luger (Used) - Image 4
rhc62vwjq25n52umfmfkm4yq7yuxwuk6bjduyvzjzhb3cyhp2q65m2qd.onion

SIG Sauer P-220 9mm Luger (Used) - Image 4
rhc62vwjq25n52umfmfkm4yq7yuxwuk6bjduyvzjzhb3cyhp2q65m2qd.onion

SIG Sauer P-220 9mm Luger (Used) - Image 2
rhc62vwjq25n52umfmfkm4yq7yuxwuk6bjduyvzjzhb3cyhp2q65m2qd.onion

SIG Sauer P-220 9mm Luger (Used) - Image 2
rhc62vwjq25n52umfmfkm4yq7yuxwuk6bjduyvzjzhb3cyhp2q65m2qd.onion

SIG Sauer P-220 9mm Luger (Used) - Image 3
rhc62vwjq25n52umfmfkm4yq7yuxwuk6bjduyvzjzhb3cyhp2q65m2qd.onion