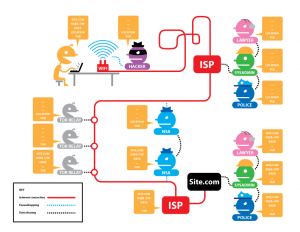
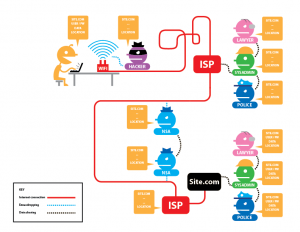
About 35,224 results found.
(Query 0.02000 seconds)
- All
- Images

Service: Hacked Social Media Accounts
5odv4qjwkhpv3obbtqlgjsk3xfcr6llfvu6dfn6u4e5umhjd3flikgid.onion
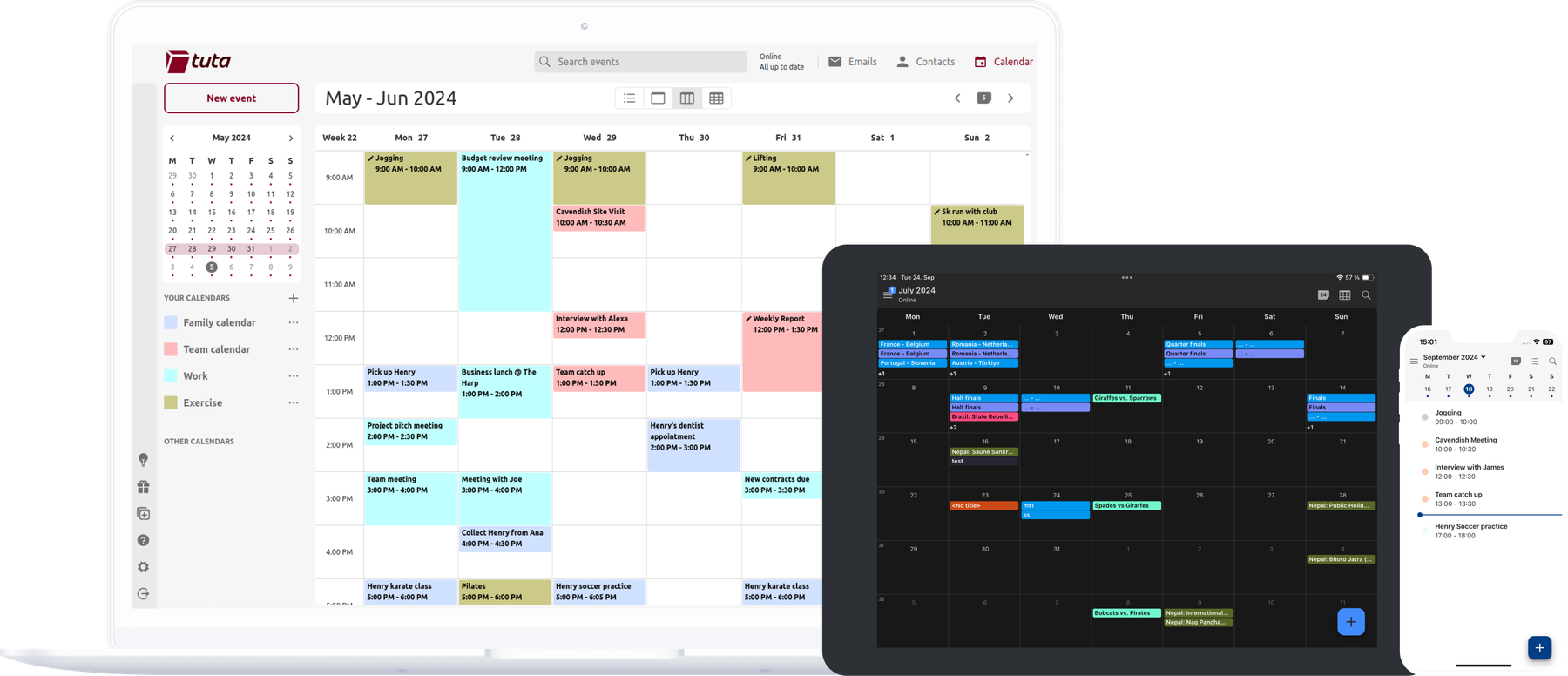
Komposition des Tuta-Kalenders in seinem neuen Look auf Desktop, iPad und iPhone.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 100
bmguns3cak7kl7ksin2vho2gstg7vfz2lhr5s5aiiyfhfrfeevbtquid.onion

CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 100
bmguns3cak7kl7ksin2vho2gstg7vfz2lhr5s5aiiyfhfrfeevbtquid.onion

CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 100
bmguns3cak7kl7ksin2vho2gstg7vfz2lhr5s5aiiyfhfrfeevbtquid.onion

CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 100
bmguns3cak7kl7ksin2vho2gstg7vfz2lhr5s5aiiyfhfrfeevbtquid.onion

CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 100
bmguns3cak7kl7ksin2vho2gstg7vfz2lhr5s5aiiyfhfrfeevbtquid.onion

Exploring Alternative Cryptocurrencies for Privacy and Security
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Exploring Cryptographic Hash Functions: What Every Beginner Should Know
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Using VPNs with Tor: Is It Necessary and How to Do It Right?
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion
Tutanota encrypted email client in 2020
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Tor Browser Downloader (Whonix) Download Confirmation
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion
torbrowser-updater_signature_verification_screen.
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion

Buy Asos $500 from the trusted seller CHICHI | TorBuy - The best escrow marketplace with verified sellers.
torbuyec4aetakqpuw4tnvkimrl77tj4qrhx74mgmu6lqmdxvp27jqyd.onion

Buy Paypal 1800 dollars from the trusted seller PayPal mania | TorBuy - The best escrow marketplace with verified sellers.
torbuyec4aetakqpuw4tnvkimrl77tj4qrhx74mgmu6lqmdxvp27jqyd.onion

Avoiding Scams on the Dark Web: What Every Beginner Should Know
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion
How to Protect Your Identity and Avoid Tracking While on the Dark Web
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

How to Safely Share Encrypted Files Over Public Channels
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Setting Up and Configuring Whonix for Maximum Privacy
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion