About 17,352 results found.
(Query 0.01200 seconds)
- All
- Images
Browser Fingerprints: Crucial Podcast
privacyy3tsy4mge4qmg4nsid2vnhl7szzupphhkfsxvayx5tl2ztbqd.onion

Image: South African flag with a digital Bitcoin symbol, emphasizing how to buy BTC via Coinmama.
coinmamailtcrg7fw6uorut3d35bk35rtmntkrtb4fgeov6pefvfutqd.onion

A person uses a Bitcoin ATM near greenery to buy crypto effortlessly via Coinmama.
coinmamailtcrg7fw6uorut3d35bk35rtmntkrtb4fgeov6pefvfutqd.onion
Encrypted WhatsApp alternative Businesses: Wire.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Best replacement for open source: Element app by matrix.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Up-and-coming Decentralized WhatsApp Alternative: SimpleX.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Telegram - is it better than WhatsApp?
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
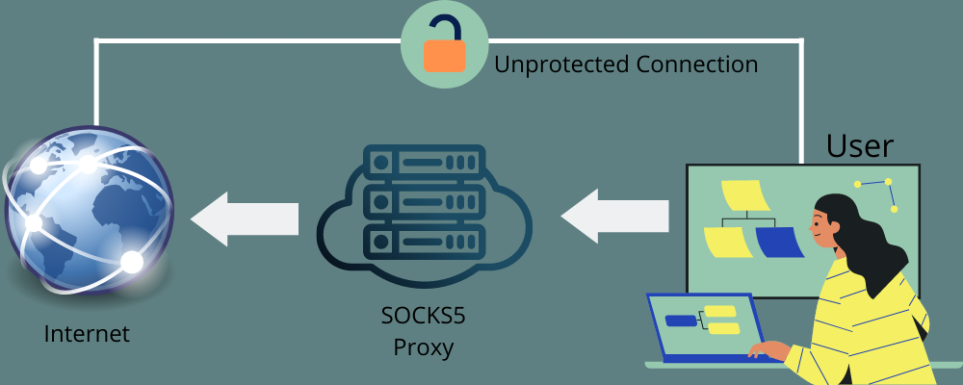
Socks5 Proxy vs VPN: What's the Difference?
privacyy3tsy4mge4qmg4nsid2vnhl7szzupphhkfsxvayx5tl2ztbqd.onion

An illustration showcases a person with large "S" and scattered coins, emulating Coinmama's buy crypto platform.
coinmamailtcrg7fw6uorut3d35bk35rtmntkrtb4fgeov6pefvfutqd.onion
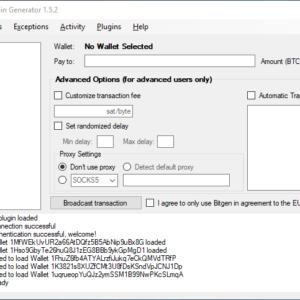
Bitcoin Fake Transaction vector 76 attack
dreamr6y7e7ilemgws2ccuegvwdge3sfdm2ijh4s4hc2eggz3cvgl2ad.onion

Exploring Alternative Cryptocurrencies for Privacy and Security
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Exploring Cryptographic Hash Functions: What Every Beginner Should Know
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Using VPNs with Tor: Is It Necessary and How to Do It Right?
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

How to Safely Share Encrypted Files Over Public Channels
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Setting Up and Configuring Whonix for Maximum Privacy
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

How to Protect Your Cryptographic Keys From Being Compromised
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion
Is Your Smartphone Compromising Your OpSec? Tips for Secure Mobile Usage
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Encrypted Messages in Public Spaces: The Modern Dead Drop
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion