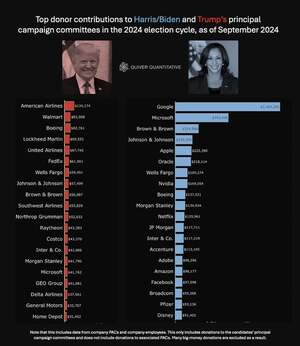
About 9,507 results found.
(Query 0.00400 seconds)
- All
- Images

The angular outline of three faces as a computer might see them, colored like a rainbow
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Exploring Alternative Cryptocurrencies for Privacy and Security
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Exploring Cryptographic Hash Functions: What Every Beginner Should Know
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Using VPNs with Tor: Is It Necessary and How to Do It Right?
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Avoiding Scams on the Dark Web: What Every Beginner Should Know
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion
How to Protect Your Identity and Avoid Tracking While on the Dark Web
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

How to Safely Share Encrypted Files Over Public Channels
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Setting Up and Configuring Whonix for Maximum Privacy
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

How to Protect Your Cryptographic Keys From Being Compromised
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion
Is Your Smartphone Compromising Your OpSec? Tips for Secure Mobile Usage
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion

Encrypted Messages in Public Spaces: The Modern Dead Drop
bkg5ofjslnbyqvu55sjonpdyp3wmfsgq23u7vpk3wxn7ewgdeocpgwid.onion
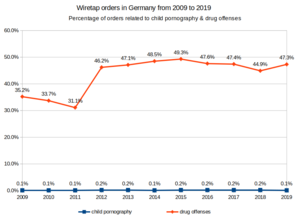
Comparison of the percentage of wiretap orders for child pornography and drug offenses in Germany, 2009-2019.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
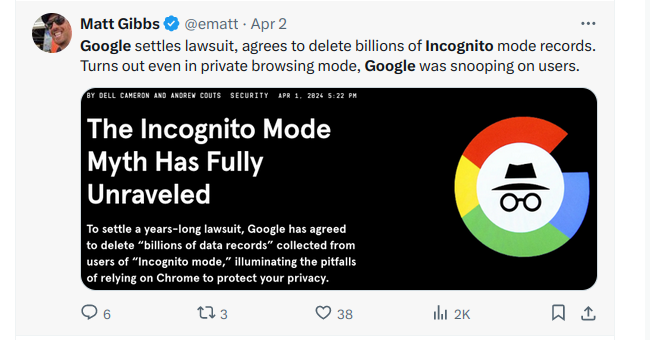
Google legt den Rechtsstreit um den Inkognito-Modus bei und erklärt sich bereit, Daten zu löschen.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Privacy win: Court rules that Google tricked people with Incognito Mode.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Encrypt the Web (security hole)
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion